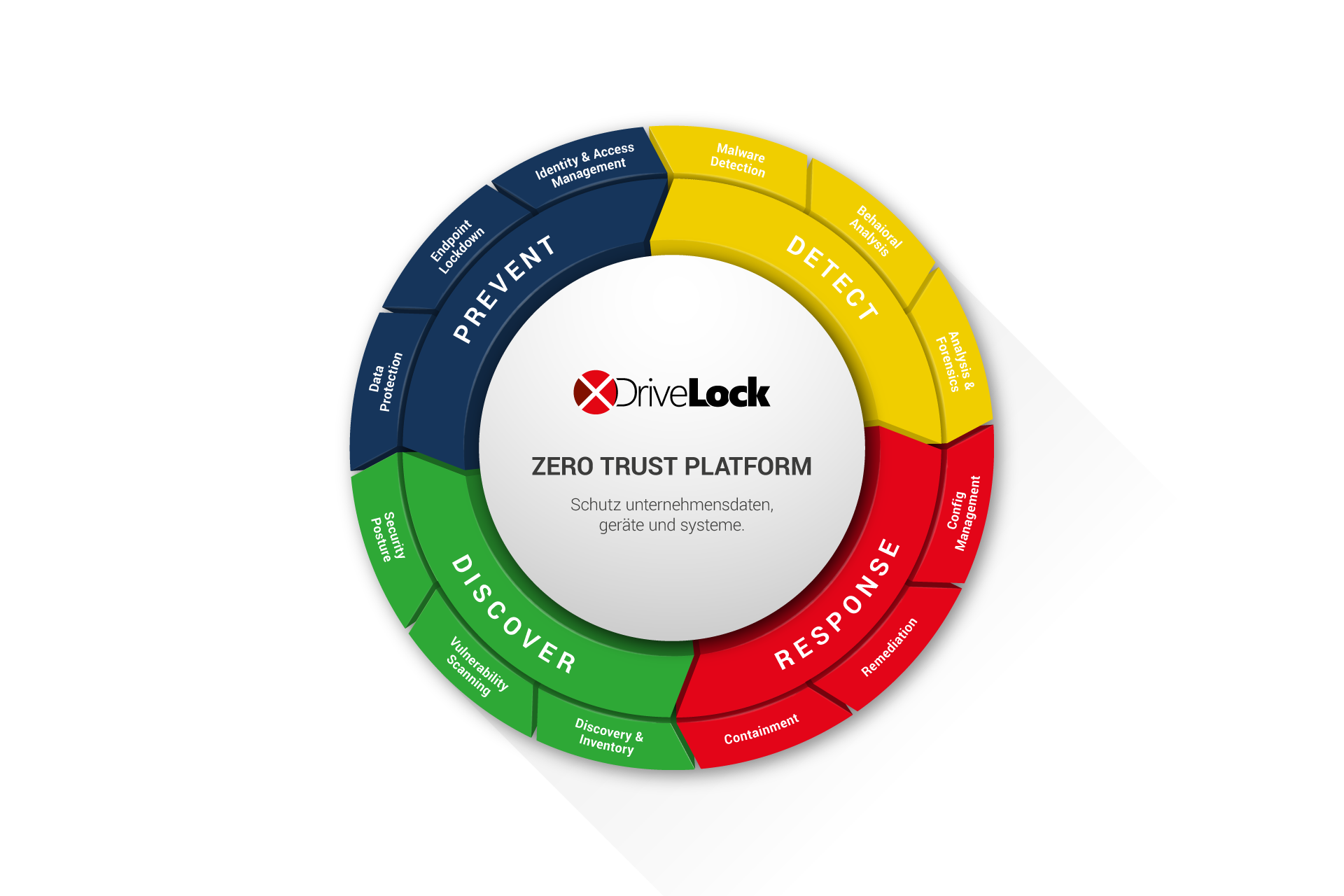
Graphic that shows the modules/functions of a software platform
46
Created on 99designs by Vista
The graphic is to be used in PowerPoint presentations, on the website and in brochures. The background to this graphic is as follows: The strategy in IT security today works according to the so-called "zero trust model".